Google Cloud Platform
This guide describes how to run QuestDB on a Compute Engine instance on Google Cloud platform with details on how to enable networking on various interfaces by means of firewall rules.
This guide uses the official QuestDB Docker image during VM instance creation to simplify setup steps for a quick, robust deployment. The networking rules below show how to make ports for PostgreSQL wire protocol and REST API publicly accessible or by whitelisted IP.
Prerequisites#
- A Google Cloud Platform (GCP) account and a GCP Project
- The Compute Engine API must be enabled for the corresponding Google Cloud Platform project
Create a Compute Engine VM#
- In the Google Cloud Console, navigate to Compute Engine and click Create Instance
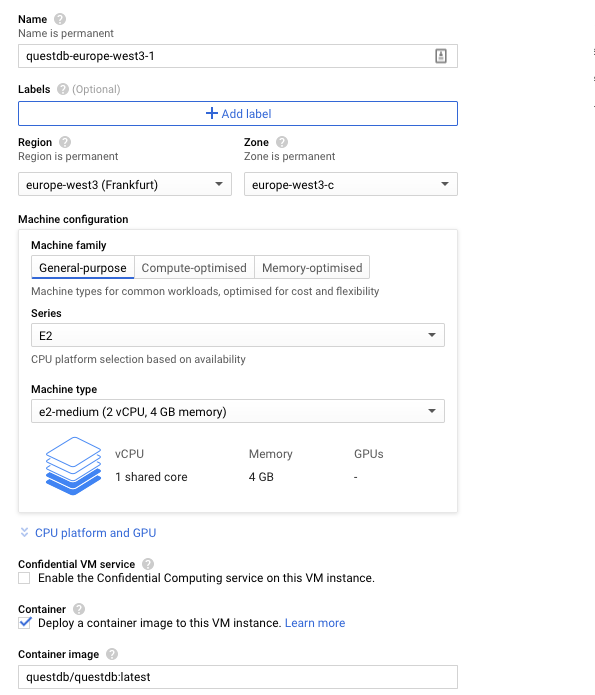
Give the instance a name, this example uses
questdb-europe-west3Choose a Region and Zone, this example uses
europe-west3 (Frankfurt)and the default zoneChoose a machine configuration, a general-purpose instance is
e2-mediumwith 4GB memoryEnable the checkbox under Container and provide the latest QuestDB Docker image:
Given the steps so far, the VM Instance configuration page should look like the following:
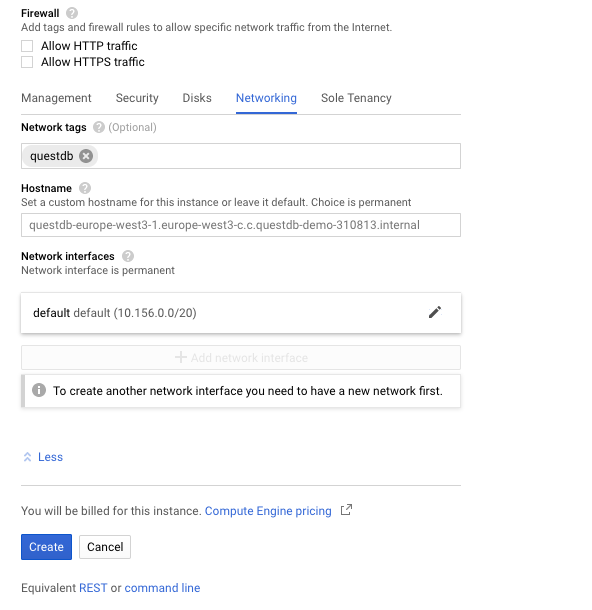
Before creating the instance, assign a Network tag so that a firewall rule for networking can be easily applied to instances of the same type.
- Expand the menu item Management, security, disks, networking, sole tenancy towards the bottom of the page
- In the Networking panel add a Network tag to identify the instance,
this example uses
questdb - Launch the instance by clicking Create
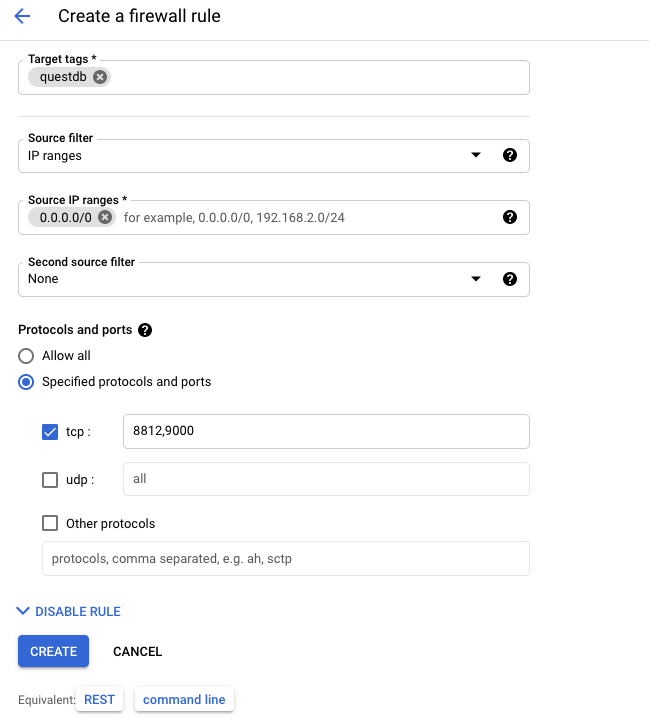
Create a firewall rule#
- Navigate to the Firewalls configuration page under VPC network -> Firewalls
- Add the target tag
questdb - Choose an IP range that this rule applies to, this example uses
0.0.0.0/0(i.e. any IP) - In the Protocols and ports section, enable
8812and9000for TCP. - Click create
All VM instances on Compute Engine within this account which have the Network
tag questdb will have this firewall rule applied.
info
The configuration above allows networking from any IP address for the selected ports. A more secure approach would be to only allow incoming connections from whitelisted IPs.
The ports we have opened are
9000for the REST API and Web Console8812for PostgreSQL wire protocol
Verify the deployment#
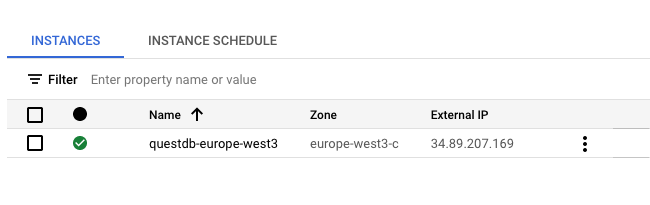
To verify the instance state, navigate to Compute Engine -> VM Instances. A status indicator should show the instance as running:
To verify that the QuestDB deployment is operating as expected:
- Copy the External IP of the instance
- Navigate to
<external_ip>:9000in a browser
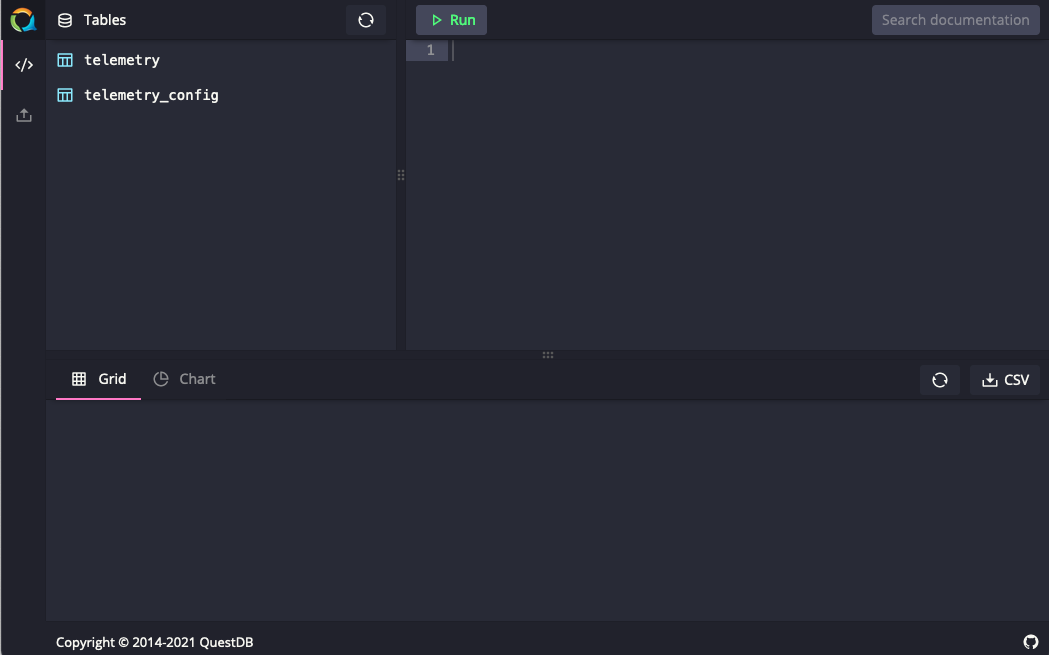
The Web Console should be visible:
Alternatively, a request may be sent against the REST API exposed on port 9000: